Clik here to view.
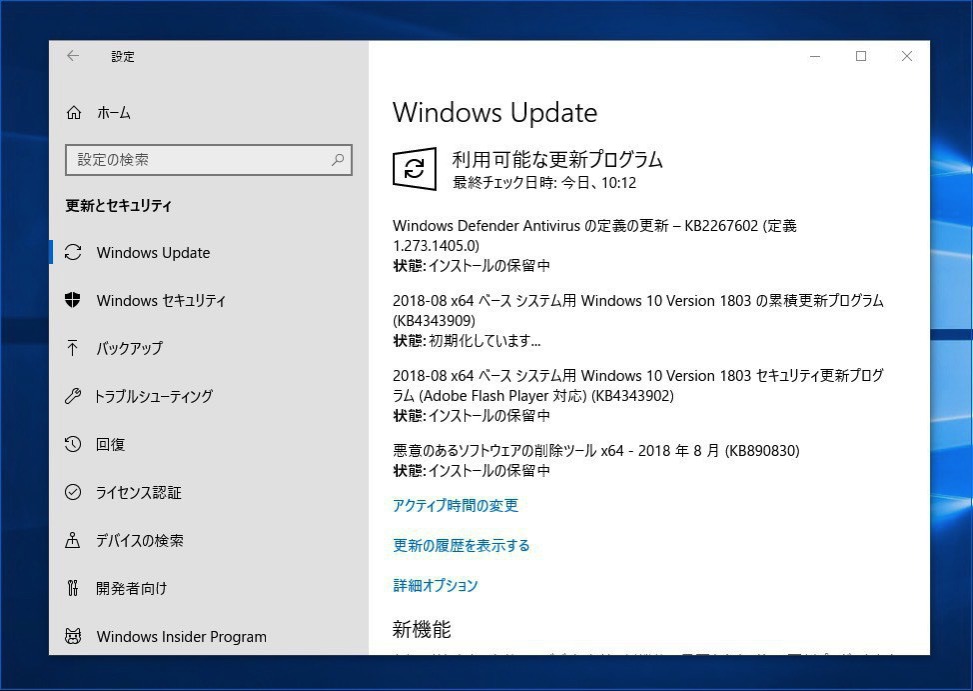
Microsoftは本日、Windows 10 Version 1803(Windows 10 April 2018 Update)用の累積アップデートKB4343909をリリースしました(Neowin)。
毎月第2火曜日(米国時間)に公開される月例更新の一貫として公開されたアップデートで、Version 1709用のKB4343897、Version 1703用のKB4018124、Version 1607用のKB4000825、RTM用のKB4343892も同時に公開されています。なお一般ユーザー向けの累積的更新プログラムの提供はVersion 1703までとなっています。Windows 10のバージョンごとのサポート期間はWindows ライフサイクルのファクト シートでご確認ください。
更新プログラムはシステムの品質を改善するもので、新たな機能は追加されていません。
それぞれWindows Updateを利用して導入することが可能で、変更内容は以下の通りです。
KB4343909 (OS Build 17134.228)
Version 1803用の累積アップデートKB4343909では、Intel Core/Xenonプロセッサに影響を与える新しい投機的実行サイドチャンネル脆弱性に対する保護の提供や、一部のAMDプロセッサでCPUの使用率が高くなり処理性能が低下する問題の修正、レジューム後アプリがメッシュ更新を受け取れない問題の修正などが行われています。
- Provides protections against a new speculative execution side-channel vulnerability known as L1 Terminal Fault (L1TF) that affects Intel® Core® processors and Intel® Xeon® processors (CVE-2018-3620 and CVE-2018-3646). Make sure previous OS protections against Spectre Variant 2 and Meltdown vulnerabilities are enabled using the registry settings outlined in the Windows Client and Windows Server guidance KB articles. (These registry settings are enabled by default for Windows Client OS editions, but disabled by default for Windows Server OS editions.)
- Addresses an issue that causes high CPU usage that results in performance degradation on some systems with Family 15h and 16h AMD processors. This issue occurs after installing the June 2018 or July 2018 Windows updates from Microsoft and the AMD microcode updates that address Spectre Variant 2 (CVE-2017-5715 – Branch Target Injection).
- Addresses an issue that prevents apps from receiving mesh updates after resuming. This issue occurs for apps that use Spatial Mapping mesh data and participate in the Sleep or Resume cycle.
- Ensures that Internet Explorer and Microsoft Edge support the preload="none" tag.
- Addresses an issue that prevents some applications running on HoloLens, such as Remote Assistance, from authenticating after upgrading from Windows 10, version 1607, to Windows 10, version 1803.
- Addresses an issue that significantly reduced battery life after upgrading to Windows 10, version 1803.
- Addresses an issue that causes Device Guard to block some ieframe.dll class IDs after installing the May 2018 Cumulative Update.
Addresses a vulnerability related to the Export-Modulemember() function when used with a wildcard (*) and a dot-sourcing script. After installing this update, existing modules on devices that have Device Guard enabled will intentionally fail. The exception error is “This module uses the dot-source operator while exporting functions using wildcard characters, and this is disallowed when the system is under application verification enforcement.” For more information, see https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2018-8200 and https://aka.ms/PSModuleFunctionExport.
Addresses an issue that was introduced in the July 2018 .NET Framework update. Applications that rely on COM components were failing to load or run correctly because of “access denied,” “class not registered,” or “internal failure occurred for unknown reasons” errors.
- Security updates to Windows Server.
既知の不具合は存在せず、更新プログラムはMicrosoft Update Catalogから入手することも可能です。
KB4343897 (OS Build 16299.611)
Version 1709用の累積アップデートKB4343897では、Intel Core/Xenonプロセッサに影響を与える新しい投機的実行サイドチャンネル脆弱性に対する保護の提供や、一部のAMDプロセッサでCPUの使用率が高くなり処理性能が低下する問題の修正、トークンバインディングプロトコルv0.16のドラフト版のサポートするための更新などが行われています。
- Provides protections against a new speculative execution side-channel vulnerability known as L1 Terminal Fault (L1TF) that affects Intel® Core® processors and Intel® Xeon® processors (CVE-2018-3620 and CVE-2018-3646). Make sure previous OS protections against Spectre Variant 2 and Meltdown vulnerabilities are enabled using the registry settings outlined in the Windows Client and Windows Server guidance KB articles. (These registry settings are enabled by default for Windows Client OS editions, but disabled by default for Windows Server OS editions.)
- Addresses an issue that causes high CPU usage that results in performance degradation on some systems with Family 15h and 16h AMD processors. This issue occurs after installing the June 2018 or July 2018 Windows updates from Microsoft and the AMD microcode updates that address Spectre Variant 2 (CVE-2017-5715 – Branch Target Injection).
- Updates support for the draft version of the Token Binding protocol v0.16.
- Addresses an issue that causes Device Guard to block some ieframe.dll class IDs after the May 2018 Cumulative Update is installed.
- Ensures that Internet Explorer and Microsoft Edge support the preload="none" tag.
- Addresses an issue that displays “AzureAD” as the default domain on the sign-in screen after installing the July 24, 2018 update on a Hybrid Azure AD-joined machine. As a result, users may fail to sign in in Hybrid Azure AD-joined scenarios when users provide only their username and password.
- Addresses an issue that adds additional spaces to content that's copied from Internet Explorer to other apps.
Addresses a vulnerability related to the Export-Modulemember() function when used with a wildcard (*) and a dot-sourcing script. After installing this update, existing modules on devices that have Device Guard enabled will intentionally fail. The exception error is “This module uses the dot-source operator while exporting functions using wildcard characters, and this is disallowed when the system is under application verification enforcement”. For more information, see https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2018-8200 and https://aka.ms/PSModuleFunctionExport.
Addresses an issue that was introduced in the July 2018 .NET Framework update. Applications that rely on COM components were failing to load or run correctly because of “access denied,” “class not registered,” or “internal failure occurred for unknown reasons” errors.
Security updates to Windows Server.
更新プログラムには、特定のメッセージがローカライズされた言語ではなく、英語で表示される既知の不具合が二件掲載されています。更新プログラムはMicrosoft Update Catalogからダウンロードすることもできます。
KB4343885 (OS Build 15063.1266)
Version 1703用の累積アップデートKB4343885では、Intel Core/Xenonプロセッサに影響を与える新しい投機的実行サイドチャンネル脆弱性に対する保護の提供や、Internet Explorerの動作が一部Webサイトで停止する問題の修正、トークンバインディングプロトコルv0.16のドラフト版のサポートするための更新などが行われています。
Provides protections against a new speculative execution side-channel vulnerability known as L1 Terminal Fault (L1TF) that affects Intel® Core® processors and Intel® Xeon® processors (CVE-2018-3620 and CVE-2018-3646). Make sure previous OS protections against Spectre Variant 2 and Meltdown vulnerabilities are enabled using the registry settings outlined in the Windows Client guidance KB article. (These registry settings are enabled by default for Windows Client OS editions.)
- Addresses an issue that causes Internet Explorer to stop working for certain websites.
- Updates support for the draft version of the Token Binding protocol v0.16.
- Addresses an issue that causes Device Guard to block some ieframe.dll class IDs after installing the May 2018 Cumulative Update.
- Ensures that Internet Explorer and Microsoft Edge support the preload="none" tag.
Addresses a vulnerability related to the Export-Modulemember() function when used with a wildcard (*) and a dot-sourcing script. After installing this update, existing modules on devices that have Device Guard enabled will intentionally fail. The exception error is “This module uses the dot-source operator while exporting functions using wildcard characters, and this is disallowed when the system is under application verification enforcement”. For more information, see https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2018-8200 and https://aka.ms/PSModuleFunctionExport.
Addresses an issue that was introduced in the July 2018 .NET Framework update. Applications that rely on COM components were failing to load or run correctly because of “access denied,” “class not registered,” or “internal failure occurred for unknown reasons” errors.
- Security updates to Windows Server.
既知の不具合は存在せず、更新プログラムはMicrosoft Update Catalogから入手することも可能です。
セキュリティアップデートの内容はMicrosoftのブログなどから参照することができます。